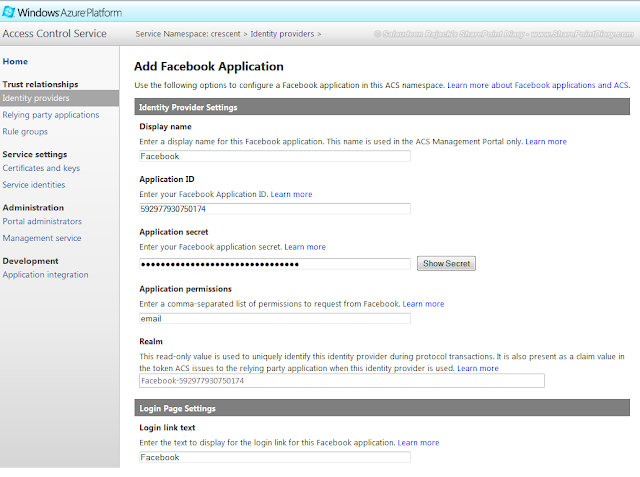
Configure outgoing Email settings using Gmail in SharePoint
Open Server Manager and then click on Add roles and features
under Configure this local server as shown in the fig below:
Then in the Add Roles and Features Wizard click on Next, In the
Installation Type, select Role-based or feature-based installation. And then
click on Next. In the Server selection select the server (default also
selected) and then click on Next. Do not do anything in the Server Roles click
Next to go to Features. There check the check box SMTP server Then it will ask
for Add features that are required for SMTP server? Click on Add Features. And
click on Install. After this we do not need to do anything in this step, just
wait that to finish.
Once finish, Put cursor at right corner of the windows
server 2012 and there click on the Search Icon. In the search box type IIS and
then Click on Internet Information Services (IIS) 6.0 Manager.
This will open Internet Information Services (IIS) 6.0 Manager,
Expand the server and Right click on SMTP Virtual server and Select Start as
shown in the fig below:
Again Right click on SMTP Virtual server click on Properties.
This will open the [SMTP Virtual server #1] properties dialog box.
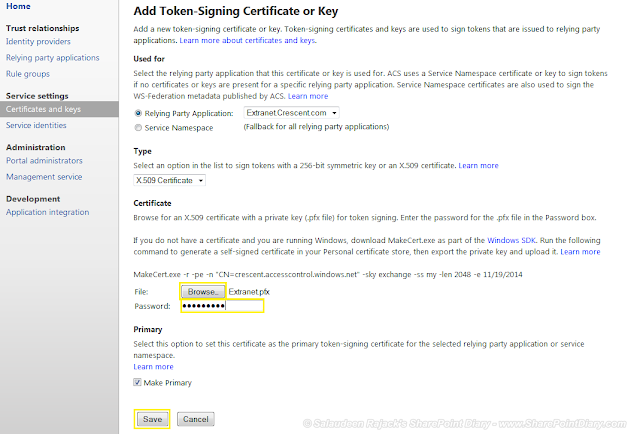
In the General Tab, Click on Advanced... button and it will open
the Indentification dialog box, IP address (All Unassigned) and then in the TCP
port put 587 and click on OK.
Then click on the Access tab from the [SMTP Virtual server #1]
properties dialog box. Here click on Authentication... button. Then in the
Authentication dialog box, check the Anonymous access check box as shown in the
fig below.
Then click on the Connections button and select radio button All
Except the list below and click on OK as shown in the fig below.
Then click on Relay... button.
Then in the Relay Restrictions dialog box select All
Except the list below button as shown in the fig below and click on OK.
Then go to the Delivery tab and on the Delivery tab, click on
Outbound Security, on the new window that opens select Basic Authentication and
type your Gmail email and password in the Username and Password fields, and
also select TLS encryption
Then on the Delivery tab, click Outbound connections… and in the
new Outbound connections change TCP port to 587 as shown in the fig below:
Then in the Advanced... button, In the Delivery tab, click on
Advanced... button and in the Advanced Delivery dialog box in the Smart host
field type smtp.gmail.com and in the Fully-qualified domain
name, give system name click OK as shown in the fig below.
Then click on Apply and OK.
But here POP should be enabled in Gmail Account. That we can
found in Gmail -> Settings -> Forwarding and POP/IMAP.
Now Open SharePoint Central Administration then go to System
Settings. And then Click on Configure outgoing e-mail settings as shown in the
fig below:
Then in the Outgoing E-Mail Settings, give Outbound SMTP server
as smtp.gmail.com, From address as: abc@gmail.com and click on OK as
shown in the fig below:
This finishes our configuration.